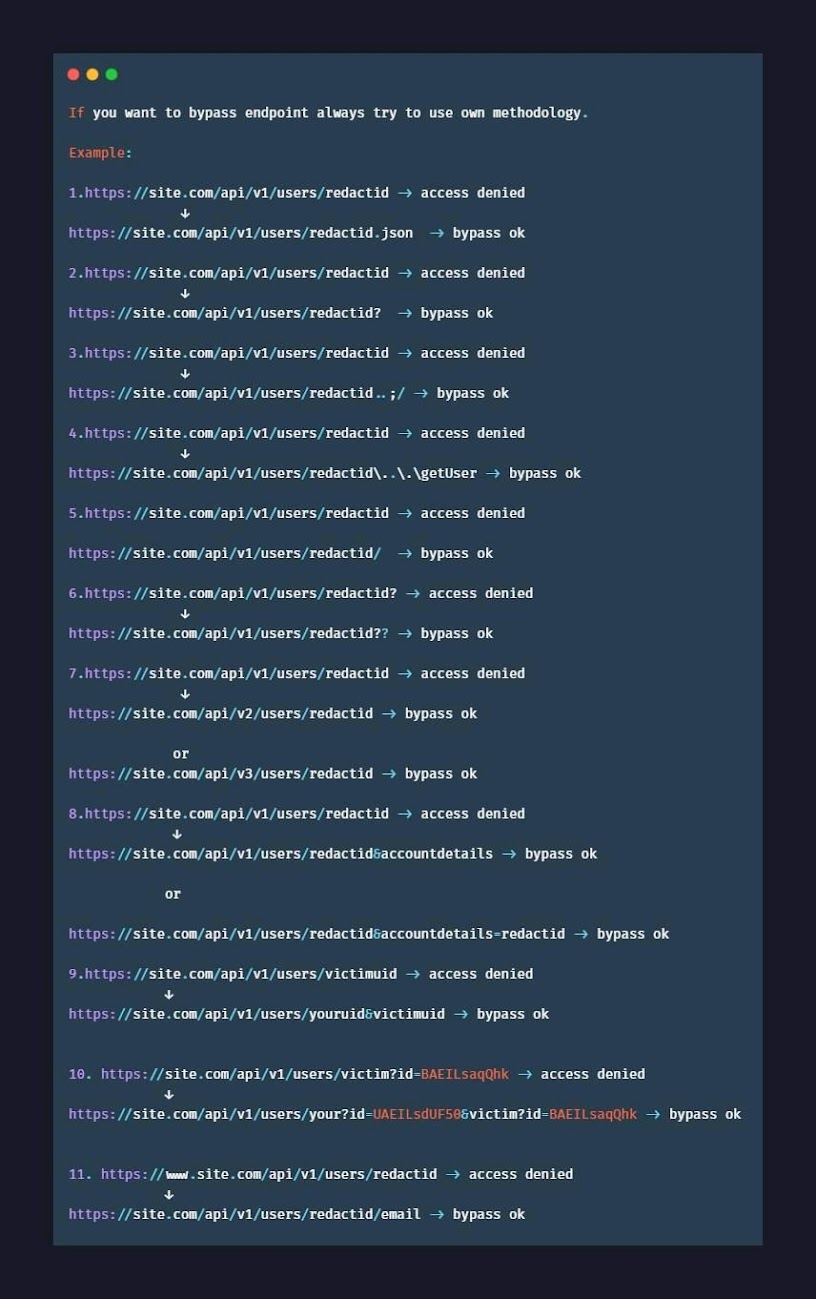
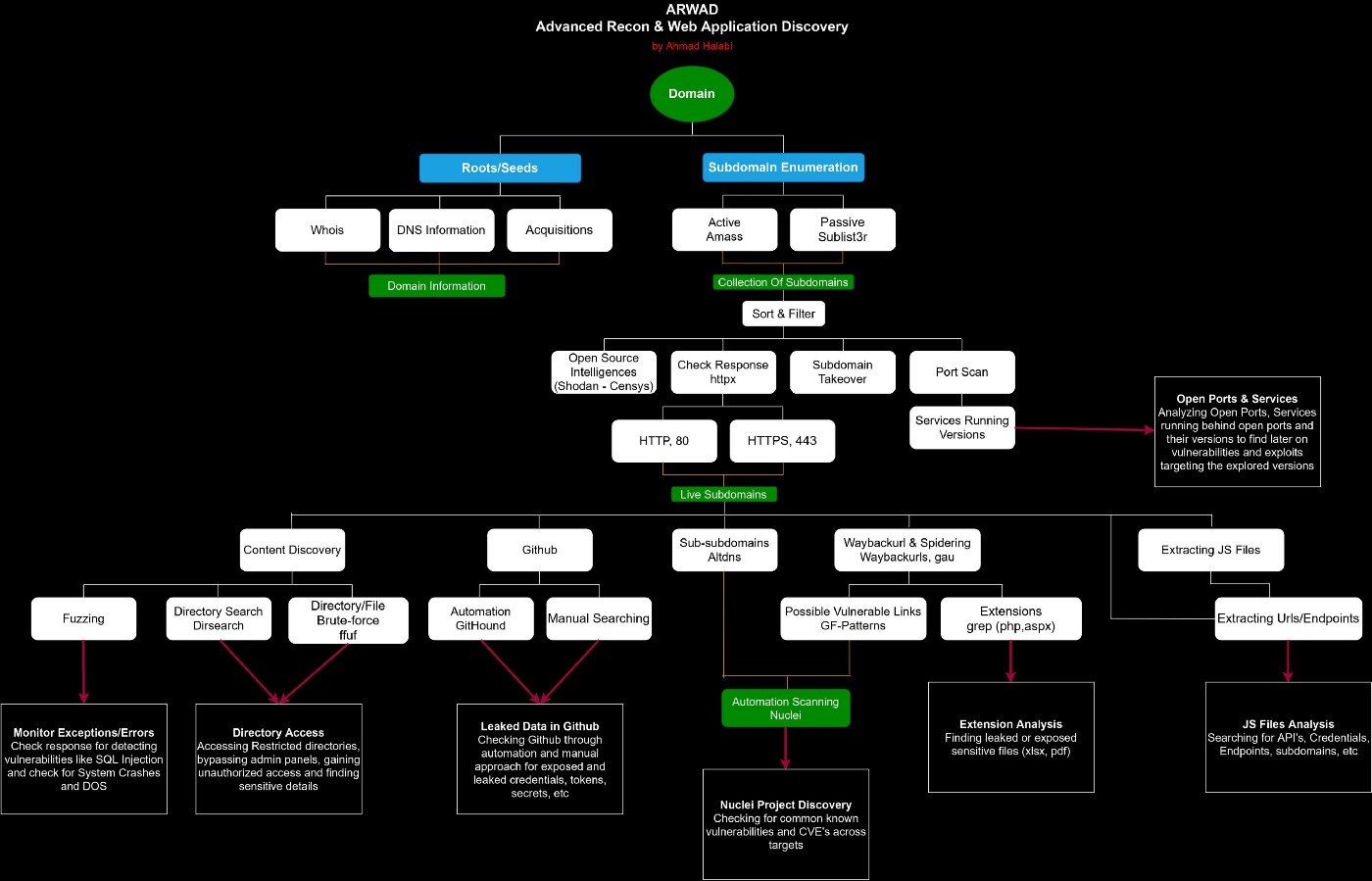
Know what is Shodan Exactly !

What Is Shodan Exactly? Shodan is a search engine for Internet-connected devices. It is different from search engines like Google and Bing because Google and Bing are great for finding websites but Shodan helps in finding different things like popular versions of Microsoft IIS, control servers for Malware, how many host are affected with the new CVEs, which countries are becoming more connected, SSL certificates of the websites etc. Difference between Shodan and Google : The major difference between Shodan and Google is that, that Shodan analyzes the internet and Google analyzes the Word Wide Web. Description : Shodan is the most popular search engine ever seen. It has the capability to index small desktops, CCTVs, nuclear power plants etc. Nowadays shodan has become very popular in the world of penetration testing, bug bounties, digital forensics, threat hunting etc. Shodan’s Search Query Insights : Shodan gathers information by interacting with web ser...