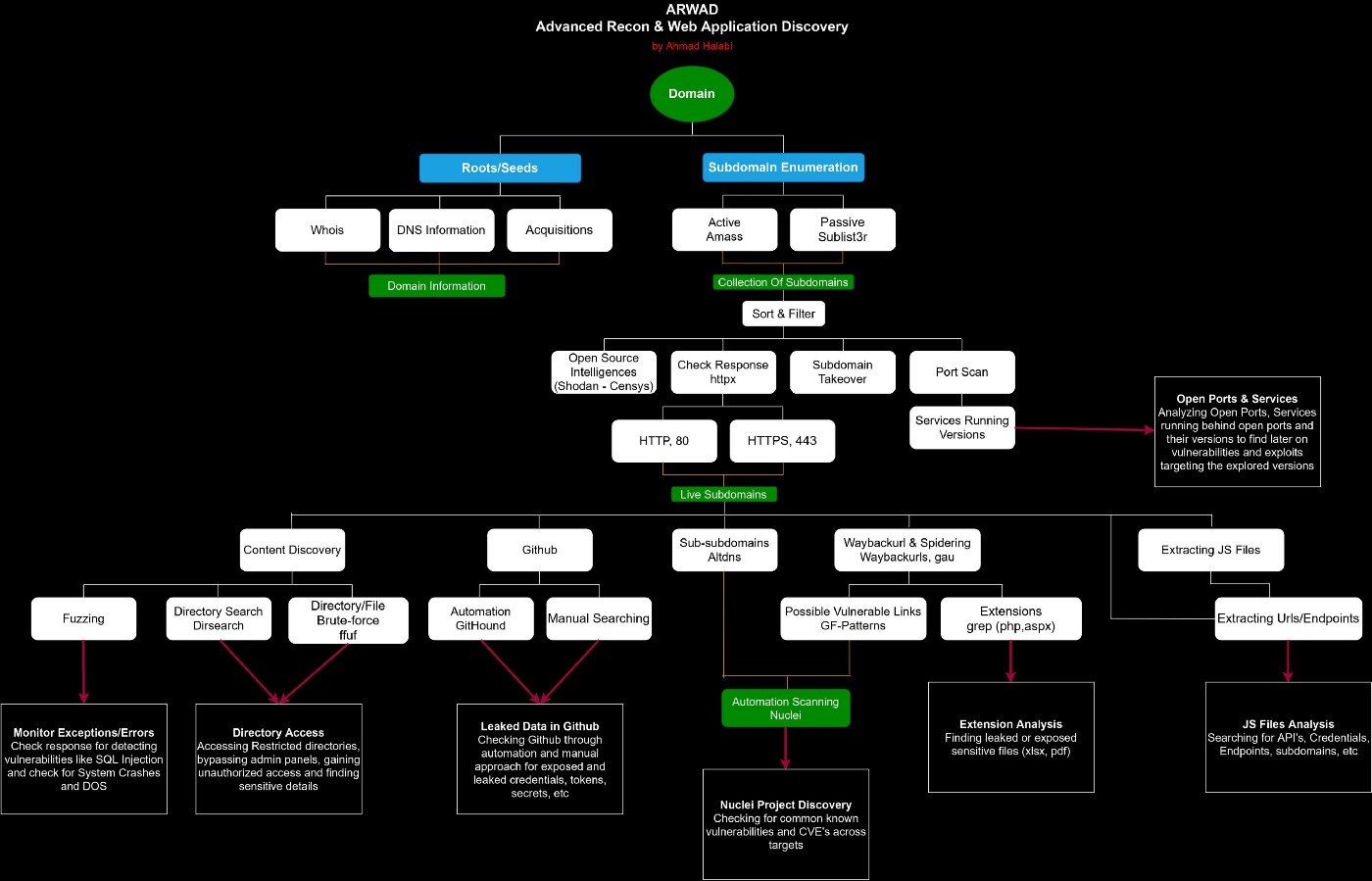
GitHub Dorking methodology
Manual Approach ;
Let’s start with how you can get sensitive information leak Sensitive information is as follows ;
"Company name" credentials
Keywords 👇
{User_names , password, token , Secret key , backup file , pwd, credentials, ftp, JDBC, LDAP, key , pass , pw, user_auth }
GitHub Dorks for Finding Files:
“company name” filename:database
“company name” filename:secrets.yml
“company name” filename:passwd
“company name” filename:LocalSettings.php
“company name” filename:config.php
“company name” filename:config.inc.php
“company name” filename:configuration.php
“company name” filename:shadow
“company name” filename:.env
“company name” filename:wp-config.php
“company name” filename:credentials
“company name” filename:id_rsa
“company name” filename:id_dsa
“company name” filename:.sqlite
“company name” filename:secret_token.rb
“company name” filename:settings.py
“company name” filename:credentials.xml
GitHub Dorks for Finding information sensitive from programming language
“Company name” language:python
“Company name” language:bash
“company name” language:shell
“company name” language:bash
“company name” language:SQL
“company name” language:Shell
GitHub dork for s3 buckets :
org:Target "bucket_name"
org:Target "aws_access_key" org:Target "aws_secret_key"
org:Target "S3_BUCKET"
org:Target "S3_ACCESS_KEY_ID"
org:Target
"S3_SECRET_ACCESS_KEY"
org:Target "S3_ENDPOINT"
org:Target
"AWS_ACCESS_KEY_ID"
org:Target "list_aws_accounts"
Image:


Thank you for sharing
ReplyDeleteNice blog dude
Delete🙏👀🙏
ReplyDeleteThank you
ReplyDeleteñoño present
ReplyDelete