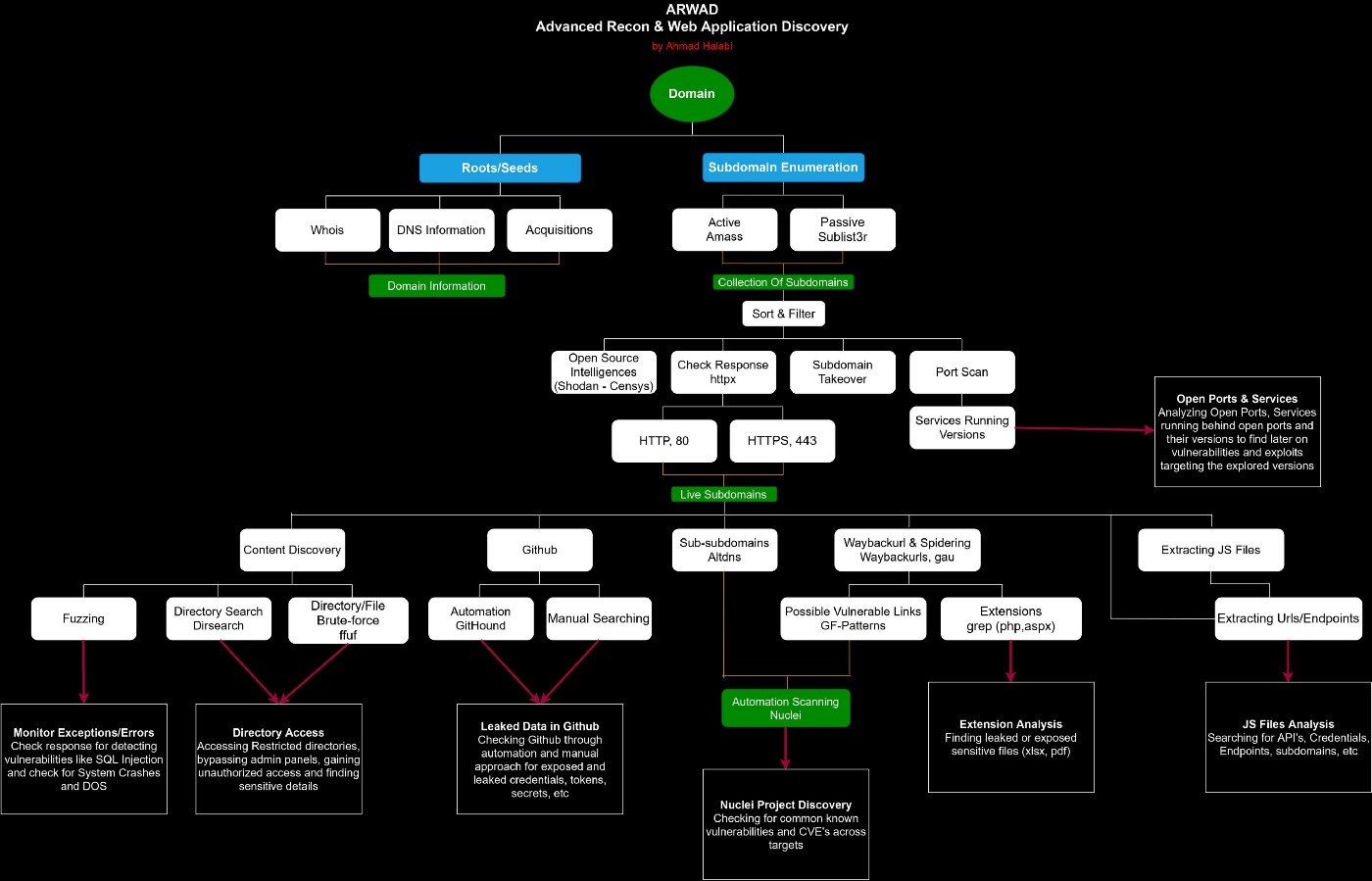
XML Attack !
What is XML external entity injection?
XML external entity injection (also known as XXE) is a web security vulnerability that allows an attacker to interfere with an application's processing of XML data. It often allows an attacker to view files on the application server filesystem, and to interact with any back-end or external systems that the application itself can access.
In some situations, an attacker can escalate an XXE attack to compromise the underlying server or other back-end infrastructure, by leveraging the XXE vulnerability to perform server-side request forgery (SSRF) attacks.
How do XML vulnerabilities arise?
While XML is an extremely popular format used by developers to transfer data between the web browser and the server, this results in XXE being a common security flaw.
XML requires a parser, which is typically where vulnerabilities occur. XXE enables an entity to be defined based on the content of a file path or URL. When the XML attack payload is read by the server, the external entity is parsed, merged into the final document, and returns it to the user with the sensitive data inside.
XXE/XML attacks can result in port scanning within the internal network, server-side request forgery (SSRF), data exfiltration, use of an organization’s servers to perform denial of service (DoS), and more.
Image: XML attack:


Comments
Post a Comment