OAuth and the flaws in its implementation
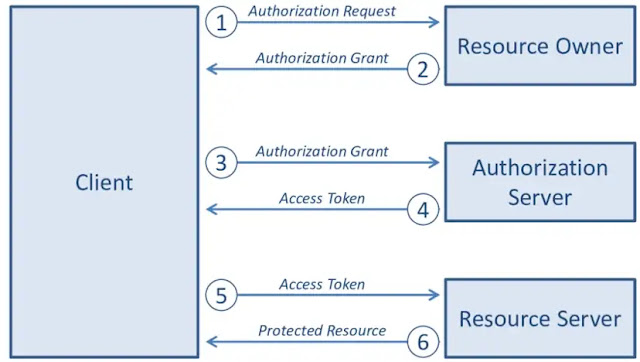
OAuth and the flaws in its implementation ! What is OAuth? Open Authorization (also known as OAuth) is an open-source framework that allows you to create accounts on websites without having to create a different user account for each website. They rely on authentic third-party websites, such as Facebook or Google, to perform the authentication process for them. It is: It is used to log into websites without the need to form an account first. Resource sharing is performed through this method. SSO is also utilised in businesses and enterprise networks for a variety of purposes (Single Sign On) Isn’t it intriguing to think about? But what are the options for gaining access to something without having to create an account? Let’s see how well it works out for you. How OAuth Works? To simplify the work flow let’s first isolate the entities involved. They are: User (i.e., you) Application that you want to access Authorization Server For example, you go to example.com. To access it...


.png)




